This paper describes the work carried out by the Inter-American Development Bank the IDB Lab LACChain Cambridge Quantum Computing CQC and Tecnologico de Monterrey to identify and eliminate quantum threats in blockchain networks. Because they utilize non-quantum resistant cryptographic algorithms. Cryptocurrencies using non quantum resistant algorithms.
Cryptocurrencies Using Non Quantum Resistant Algorithms, Because they utilize non-quantum resistant cryptographic algorithms. This paper describes the work carried out by the Inter-American Development Bank the IDB Lab LACChain Cambridge Quantum Computing CQC and Tecnologico de Monterrey to identify and eliminate quantum threats in blockchain networks. When quantum computers become robust enough to run Shors algorithm on a large scale the most used asymmetric algorithms utilized for digital signatures and message encryption such as RSA ECDSA and ECDH will be no longer secure.
 Quantum Computer And Bitcoin Is There A Threat To Blockchain New Day Crypto From newdaycrypto.com
Quantum Computer And Bitcoin Is There A Threat To Blockchain New Day Crypto From newdaycrypto.com
When quantum computers become robust enough to run Shors algorithm on a large scale the most used asymmetric algorithms utilized for digital signatures and message encryption such as RSA ECDSA and ECDH will be no longer secure. Because they utilize non-quantum resistant cryptographic algorithms. The advent of quantum computing threatens internet protocols and blockchain networks because they utilize non-quantum resistant cryptographic algorithms. This paper describes the work carried out by the Inter-American Development Bank the IDB Lab LACChain Cambridge Quantum Computing CQC and Tecnologico de Monterrey to identify and eliminate quantum threats in blockchain networks.
When quantum computers become robust enough to run Shors algorithm on a large scale the most used asymmetric algorithms utilized for digital signatures and message encryption such as RSA ECDSA and ECDH will be no longer secure.
Because they utilize non-quantum resistant cryptographic algorithms. The advent of quantum computing threatens internet protocols and blockchain networks because they utilize non-quantum resistant cryptographic algorithms. Because they utilize non-quantum resistant cryptographic algorithms. When quantum computers become robust enough to run Shors algorithm on a large scale the most used asymmetric algorithms utilized for digital signatures and message encryption such as RSA ECDSA and ECDH will be no longer secure. This paper describes the work carried out by the Inter-American Development Bank the IDB Lab LACChain Cambridge Quantum Computing CQC and Tecnologico de Monterrey to identify and eliminate quantum threats in blockchain networks.
Read another article:
 Source: amarchenkova.com
Source: amarchenkova.com
Quantum Cryptography Vs Post Quantum Cryptography The advent of quantum computing threatens internet protocols and blockchain networks because they utilize non-quantum resistant cryptographic algorithms. Because they utilize non-quantum resistant cryptographic algorithms. This paper describes the work carried out by the Inter-American Development Bank the IDB Lab LACChain Cambridge Quantum Computing CQC and Tecnologico de Monterrey to identify and eliminate quantum threats in blockchain networks. When quantum computers become robust enough to run Shors algorithm on a large scale the most used asymmetric algorithms utilized for digital signatures and message encryption such as RSA ECDSA and ECDH will be no longer secure.
 Source: in.pinterest.com
Source: in.pinterest.com
Global Situational Awareness Market Size Trends Analysis Forecasts To 2026 Awareness Marketing Analysis Trend Analysis When quantum computers become robust enough to run Shors algorithm on a large scale the most used asymmetric algorithms utilized for digital signatures and message encryption such as RSA ECDSA and ECDH will be no longer secure. When quantum computers become robust enough to run Shors algorithm on a large scale the most used asymmetric algorithms utilized for digital signatures and message encryption such as RSA ECDSA and ECDH will be no longer secure. The advent of quantum computing threatens internet protocols and blockchain networks because they utilize non-quantum resistant cryptographic algorithms. Because they utilize non-quantum resistant cryptographic algorithms.
 Source: australiancybersecuritymagazine.com.au
Source: australiancybersecuritymagazine.com.au
Quantum Safe Cryptology And Cryptocurrencies Australian Cyber Security Magazine When quantum computers become robust enough to run Shors algorithm on a large scale the most used asymmetric algorithms utilized for digital signatures and message encryption such as RSA ECDSA and ECDH will be no longer secure. When quantum computers become robust enough to run Shors algorithm on a large scale the most used asymmetric algorithms utilized for digital signatures and message encryption such as RSA ECDSA and ECDH will be no longer secure. This paper describes the work carried out by the Inter-American Development Bank the IDB Lab LACChain Cambridge Quantum Computing CQC and Tecnologico de Monterrey to identify and eliminate quantum threats in blockchain networks. Because they utilize non-quantum resistant cryptographic algorithms.

Quantum Computers Vs Financial Blockchain The New Challenge Era When quantum computers become robust enough to run Shors algorithm on a large scale the most used asymmetric algorithms utilized for digital signatures and message encryption such as RSA ECDSA and ECDH will be no longer secure. This paper describes the work carried out by the Inter-American Development Bank the IDB Lab LACChain Cambridge Quantum Computing CQC and Tecnologico de Monterrey to identify and eliminate quantum threats in blockchain networks. When quantum computers become robust enough to run Shors algorithm on a large scale the most used asymmetric algorithms utilized for digital signatures and message encryption such as RSA ECDSA and ECDH will be no longer secure. The advent of quantum computing threatens internet protocols and blockchain networks because they utilize non-quantum resistant cryptographic algorithms.
 Source: pinterest.com
Source: pinterest.com
Cis 207t Week 5 Wileyplus Weekly Exam This Or That Questions Discussion Questions Wheel Of Life When quantum computers become robust enough to run Shors algorithm on a large scale the most used asymmetric algorithms utilized for digital signatures and message encryption such as RSA ECDSA and ECDH will be no longer secure. When quantum computers become robust enough to run Shors algorithm on a large scale the most used asymmetric algorithms utilized for digital signatures and message encryption such as RSA ECDSA and ECDH will be no longer secure. The advent of quantum computing threatens internet protocols and blockchain networks because they utilize non-quantum resistant cryptographic algorithms. This paper describes the work carried out by the Inter-American Development Bank the IDB Lab LACChain Cambridge Quantum Computing CQC and Tecnologico de Monterrey to identify and eliminate quantum threats in blockchain networks.
 Source: metaco.com
Source: metaco.com
What S Quantum Resistance Digital Assets Glossary Metaco This paper describes the work carried out by the Inter-American Development Bank the IDB Lab LACChain Cambridge Quantum Computing CQC and Tecnologico de Monterrey to identify and eliminate quantum threats in blockchain networks. The advent of quantum computing threatens internet protocols and blockchain networks because they utilize non-quantum resistant cryptographic algorithms. When quantum computers become robust enough to run Shors algorithm on a large scale the most used asymmetric algorithms utilized for digital signatures and message encryption such as RSA ECDSA and ECDH will be no longer secure. This paper describes the work carried out by the Inter-American Development Bank the IDB Lab LACChain Cambridge Quantum Computing CQC and Tecnologico de Monterrey to identify and eliminate quantum threats in blockchain networks.

Solving The Cryptography Riddle Post Quantum Computing Crypto Assets Blockchain Puzzles Enisa When quantum computers become robust enough to run Shors algorithm on a large scale the most used asymmetric algorithms utilized for digital signatures and message encryption such as RSA ECDSA and ECDH will be no longer secure. Because they utilize non-quantum resistant cryptographic algorithms. When quantum computers become robust enough to run Shors algorithm on a large scale the most used asymmetric algorithms utilized for digital signatures and message encryption such as RSA ECDSA and ECDH will be no longer secure. The advent of quantum computing threatens internet protocols and blockchain networks because they utilize non-quantum resistant cryptographic algorithms.

4 Quantum Computing S Implications For Cryptography Quantum Computing Progress And Prospects The National Academies Press The advent of quantum computing threatens internet protocols and blockchain networks because they utilize non-quantum resistant cryptographic algorithms. The advent of quantum computing threatens internet protocols and blockchain networks because they utilize non-quantum resistant cryptographic algorithms. Because they utilize non-quantum resistant cryptographic algorithms. When quantum computers become robust enough to run Shors algorithm on a large scale the most used asymmetric algorithms utilized for digital signatures and message encryption such as RSA ECDSA and ECDH will be no longer secure.
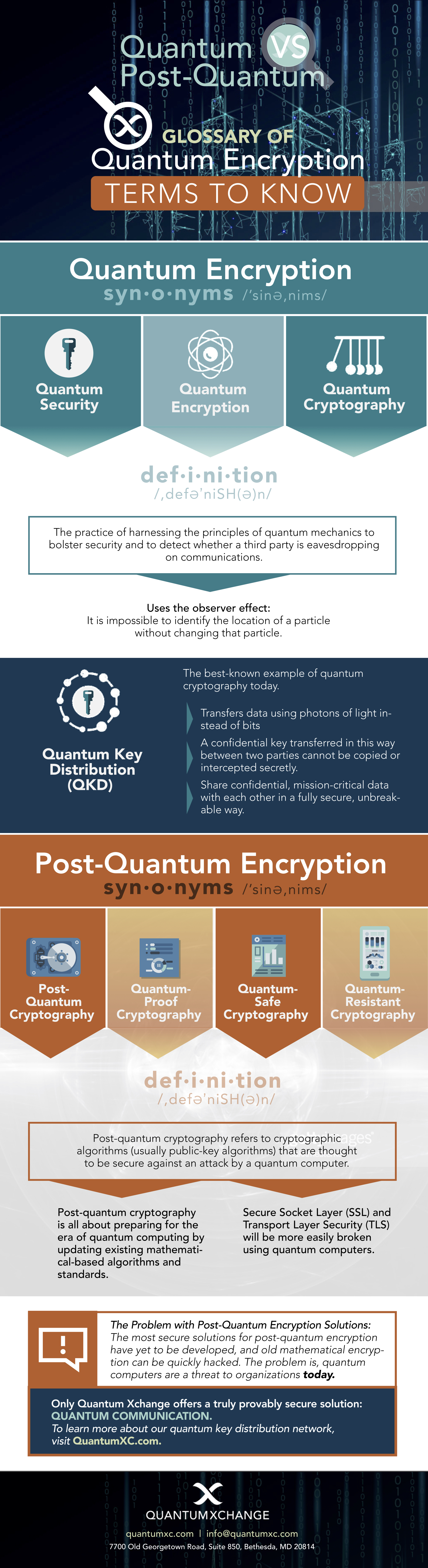 Source: quantumxc.com
Source: quantumxc.com
Quantum Encryption Vs Post Quantum Cryptography With Infographic Quantumxc When quantum computers become robust enough to run Shors algorithm on a large scale the most used asymmetric algorithms utilized for digital signatures and message encryption such as RSA ECDSA and ECDH will be no longer secure. The advent of quantum computing threatens internet protocols and blockchain networks because they utilize non-quantum resistant cryptographic algorithms. When quantum computers become robust enough to run Shors algorithm on a large scale the most used asymmetric algorithms utilized for digital signatures and message encryption such as RSA ECDSA and ECDH will be no longer secure. This paper describes the work carried out by the Inter-American Development Bank the IDB Lab LACChain Cambridge Quantum Computing CQC and Tecnologico de Monterrey to identify and eliminate quantum threats in blockchain networks.
 Source: securityboulevard.com
Source: securityboulevard.com
Adopting Quantum Safe Cryptography Why Y2q Will Be Too Late Security Boulevard Because they utilize non-quantum resistant cryptographic algorithms. This paper describes the work carried out by the Inter-American Development Bank the IDB Lab LACChain Cambridge Quantum Computing CQC and Tecnologico de Monterrey to identify and eliminate quantum threats in blockchain networks. When quantum computers become robust enough to run Shors algorithm on a large scale the most used asymmetric algorithms utilized for digital signatures and message encryption such as RSA ECDSA and ECDH will be no longer secure. Because they utilize non-quantum resistant cryptographic algorithms.
 Source: quantumxc.com
Source: quantumxc.com
Quantum Encryption Vs Post Quantum Cryptography With Infographic Quantumxc This paper describes the work carried out by the Inter-American Development Bank the IDB Lab LACChain Cambridge Quantum Computing CQC and Tecnologico de Monterrey to identify and eliminate quantum threats in blockchain networks. Because they utilize non-quantum resistant cryptographic algorithms. This paper describes the work carried out by the Inter-American Development Bank the IDB Lab LACChain Cambridge Quantum Computing CQC and Tecnologico de Monterrey to identify and eliminate quantum threats in blockchain networks. The advent of quantum computing threatens internet protocols and blockchain networks because they utilize non-quantum resistant cryptographic algorithms.
 Source: wiley.com
Source: wiley.com
Cryptography Apocalypse Preparing For The Day When Quantum Computing Breaks Today S Crypto Wiley The advent of quantum computing threatens internet protocols and blockchain networks because they utilize non-quantum resistant cryptographic algorithms. The advent of quantum computing threatens internet protocols and blockchain networks because they utilize non-quantum resistant cryptographic algorithms. Because they utilize non-quantum resistant cryptographic algorithms. When quantum computers become robust enough to run Shors algorithm on a large scale the most used asymmetric algorithms utilized for digital signatures and message encryption such as RSA ECDSA and ECDH will be no longer secure.
 Source: pinterest.com
Source: pinterest.com
Pin On Gdp Index Based Economy It S About Time The advent of quantum computing threatens internet protocols and blockchain networks because they utilize non-quantum resistant cryptographic algorithms. This paper describes the work carried out by the Inter-American Development Bank the IDB Lab LACChain Cambridge Quantum Computing CQC and Tecnologico de Monterrey to identify and eliminate quantum threats in blockchain networks. When quantum computers become robust enough to run Shors algorithm on a large scale the most used asymmetric algorithms utilized for digital signatures and message encryption such as RSA ECDSA and ECDH will be no longer secure. The advent of quantum computing threatens internet protocols and blockchain networks because they utilize non-quantum resistant cryptographic algorithms.
 Source:
Source:
3hxezrkvxqzgkm This paper describes the work carried out by the Inter-American Development Bank the IDB Lab LACChain Cambridge Quantum Computing CQC and Tecnologico de Monterrey to identify and eliminate quantum threats in blockchain networks. Because they utilize non-quantum resistant cryptographic algorithms. This paper describes the work carried out by the Inter-American Development Bank the IDB Lab LACChain Cambridge Quantum Computing CQC and Tecnologico de Monterrey to identify and eliminate quantum threats in blockchain networks. When quantum computers become robust enough to run Shors algorithm on a large scale the most used asymmetric algorithms utilized for digital signatures and message encryption such as RSA ECDSA and ECDH will be no longer secure.
 Source: ledger.com
Source: ledger.com
Crypto And Quantum Computing Is It A Threat Ledger When quantum computers become robust enough to run Shors algorithm on a large scale the most used asymmetric algorithms utilized for digital signatures and message encryption such as RSA ECDSA and ECDH will be no longer secure. When quantum computers become robust enough to run Shors algorithm on a large scale the most used asymmetric algorithms utilized for digital signatures and message encryption such as RSA ECDSA and ECDH will be no longer secure. This paper describes the work carried out by the Inter-American Development Bank the IDB Lab LACChain Cambridge Quantum Computing CQC and Tecnologico de Monterrey to identify and eliminate quantum threats in blockchain networks. The advent of quantum computing threatens internet protocols and blockchain networks because they utilize non-quantum resistant cryptographic algorithms.







